Due to cyber attacks and threats from both inside and outside the business that are continually changing, and in the new digital environment, the demand for information security managers is more important than ever. The Certified Information Security Manager (CISM) credential, offered by ISACA, is a certification that is recognized globally and an indicator of the qualification and expertise in information security management of an individual. Ideal for individuals seeking to move more into a developer or information security manager, CISM covers the management and leadership sections of the test. This blog covers everything you need to know about CISM certification, eligibility criteria, preparing for the exam, and the career advantages of being a CISM.
Understanding CISM:
The Certified Information Security Manager (CISM) is a cybersecurity certification for industry experts to design, manage, oversee, and assess enterprise information security frameworks. To become a certified professional, one must possess proper education, relevant experience, and a valid certification. Therefore, rigorous training helps candidates to gain extensive knowledge of virtual security systems, incidents and their remediation. The course thus encourages understanding and boosts confidence in cybersecurity-related domains with improved threat and incident supervision. Completion of this CISM Course ensures better career growth and opportunities in the cybersecurity domain.
Criteria to Become a CISM:

This Certified Information Security Manager Course has consistently had a high demand for learning among both amateurs and professionals. Let us understand some of the key criteria for this training that will enhance your profile and increase your visibility. Professionals with experience as Information Security Managers, IT Auditors and Consultants, Cyber Security aspirants, Network Security Engineers and Administrators, Policy Makers and Data Protection Officers, and even mid to senior level IT experts should learn this course. However, software, IT, or computer science graduates are also eligible, where they can gain in-depth knowledge through learning and training and enter the professional world.
Benefits of Obtaining CISM:
This course, being one of the most sought-after, provides access to enterprise-level cybersecurity control and management. It’s not a mere certificate, but the beginning of a strategic career progression. Here’s why:
1. Career & Financial Upside:
The UAE is now all focused on high-end digital transformation, which can bring it to the list of leading IT nations. This course will help you secure a job not just in the pure software industry, but also in all other allied industries that are being digitised. The UAE government itself is opening up numerous job opportunities that will require highly skilled system security management, alongside other sectors such as finance, gas, oil, and telecom. Professionals with this certification thus often earn an average of 4million AED annually in top markets.
2. Leadership Roles:
Completion of this course will open doors to job titles such as IT Security Manager, Risk Analyst, and Compliance Officer, particularly in Dubai and Abu Dhabi’s tech-forward enterprises.
3. Global Recognition, Local Impact:
This certification is accepted by top employers across the UAE, USA, and Europe—making you a globally mobile asset. Moreover, with more and more remote working hours becoming available, you may explore the benefits of working with USA or European MNCs from the comfort of your home. Moreover, if you are someone who loves the modern mobile nomadic life, then CISM-based career options will also remain open.
4. Executive-Level Roles:
Let’s accept the fact that we all love a higher leadership role that not just promises a fat salary but also strong recognition. This certification serves as a gateway to positions such as CISO, IT Security Director, or Information Risk Manager.
5. Skill Validation, Leadership & Credibility:
This training will validate your ability to lead security teams, manage risk, and align IT with business goals. On-the-job training, internships, and attending seminars led by industry leaders will also enhance your job applicability and performance.
6. Strategic Relevance:
You will be equipped to bridge the gap between operations and management’s work and decisions. Consequently, you will understand that ensuring cybersecurity is a boardroom priority.
7. Organisational Benefits:
Companies in the UAE are facing swelling pressure to comply with global standards. So, your learnings will help your company meet those requirements as easily as possible. If you still think that this program is just for techies, then think again. Strategy is the key, and this professional course thus equips you to become a strategist who wants to lead in securing digital ecosystems.
Steps to Become a CISM Certified Professional:
Apart from completing institutional learning and passing their exams, you can continue to enhance your professional skills with an industry-recognised certificate. Fear not, there are only a few steps to be recognised as a certificate holder. Let’s understand them:
1. Clearing the ISACA’s Test:
The test revolves around four major domains of cybersecurity, and each domain carries a certain weightage. The weightage is split amongst security governance, risk management, security program, and incident management. The weightage changes year on year and can be checked on ISACA’s website. You can always focus more on your favourite domain for better job relevance.
2. Follow professional integrity and industry best practices:
The eligibility parameter for obtaining the certificate from ISACA also encompasses maintaining your professionalism.
3. Performance and continuity of the CPE program:
To comply with an ISACA certificate, you must demonstrate a specific period of continued education in cybersecurity. Usually, the mandated CPE is of 20 contact hours yearly and 120 hours over a period of three years.
4. Minimum Work Experience Required for CISM
According to ISACA rules, evidence of work experience must be provided. You should have at least five years of work experience in the field of information security, of which three years must be in the management of the same.
5. Dispensation of Certificate:
With all the above-mentioned criteria fulfilled, you may now finally submit your application to ISACA. A nominal fee is also involved, which can be found on their website.
P.S.: For continued studies and staying on trend with every technological update, apart from just industry experience, enrolling in a course through an institute would always come in handy throughout your certification process and beyond.
Salary Scope For CISM
1. CISM Salary Based on experience
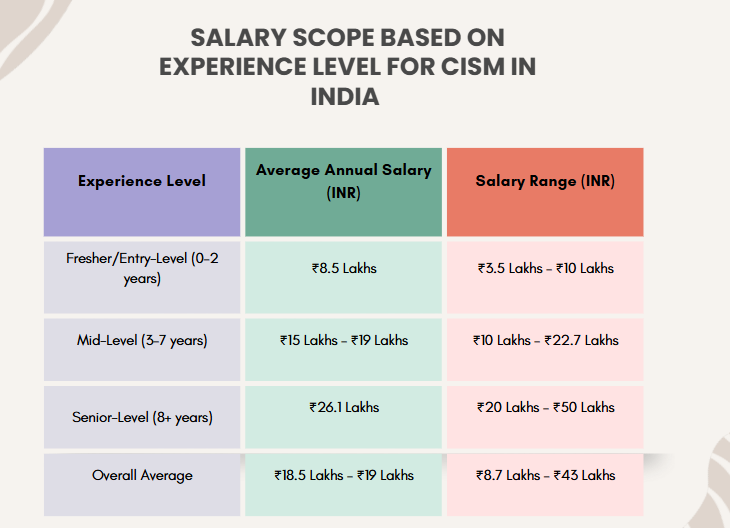
2. CISM Salary Based on the City
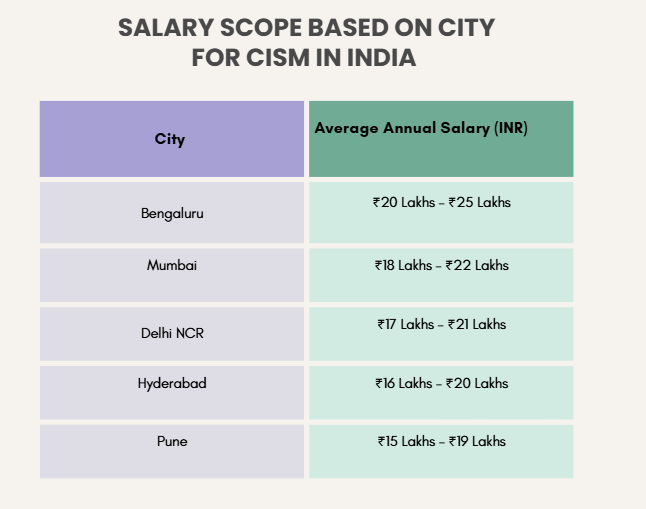
3. CISM Salary Based on Profile
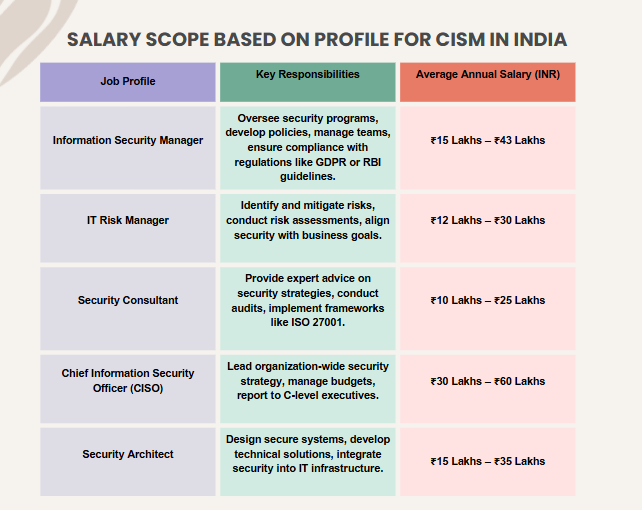
How & Where to Enrol for the CISM Course in the UAE?
There are numerous Cybersecurity Courses and CISM training institutes in the UAE today, making it challenging to select the suitable ones. To create a worthy profile, you can choose a reputable institution with a comprehensive curriculum. Offline courses can be a hassle for those already working, but others can derive significant benefits from them. Reputed institutions like Duke Training Centre and the Zabeel Institute in Dubai offer both online and offline curricula. Henry Harvin (globally recognised), GRCA Academy, and Mesk Management and Sciences Institute provide online facilities for pursuing this course. Contact them to check on the detailed CISM certification cost at their end.
Why Henry Harvin for CISM?
If you’re looking for uncompromised learning and a career leap at your own pace and comfort, Henry Harvin is the one-stop solution to your search. All the courses offered here at Henry Harvin are online, featuring self-paced learning facilities. Take a look below at the quintessential benefits that you can unlock by choosing this course with Henry Harvin:

- Get complete instructor-led sessions
- Enjoy live master sessions by industry experts
- Facilities of industry-based case studies
- Assignments and mini projects to get practical exposure to the learning experience
- Access to the job portal, placement facilities from the institute, and customised consultation related to job opportunities.
- Have your learning sessions at your own comfort and pace
- Opportunities for internships with some of the top MNCs
To unlock more facilities and options from Henry Harvin, please visit the website or contact us.
Cyber Security Course available at Henry Harvin:
In addition to this course, Henry Harvin offers a range of cybersecurity courses that may interest you. You can explore corporate Cybersecurity Training courses, postgraduate programs in Cyber Law and Security (including combined and individual courses), and a Master of Science (MS) in Cybersecurity, all of which are in demand. Enjoy learning technicalities or legal frameworks easily from the comfort of your home.
Conclusion:
This certificate will help you refine your technical skills in system security and add a niche expertise to your profile. Moreover, as this course is globally recognised, you can enjoy overseas work and recognition, along with pay enhancements and promotions. Additionally, within your own organisation, your credibility and strategic influence will increase, giving you an edge over your peers. Suppose you are already an IT professional with a pivot role in leadership in your organisation. In that case, this course will provide you with an easy launchpad to a significant role change at the industry level.
Recommended Reads:
- Mastering Cybersecurity: A Comprehensive Guide to Certified Network Defender Courses
- How to Choose the Best Cyber Security Course in UAE?
- Top 20 Cybersecurity Terms You Should Know
- Must-Know 10 Cyber Security Skills
- How to Become a Cybersecurity Analyst in 2025: A Detailed Guide?
FAQs:
Ans- The certification revolves around four core domains of Information Technology. They are the Security Governance, Risk Management, Security Program Development, and Security Incident Management.
Ans – Henry Harvin’s curriculum and study materials are more than sufficient to achieve certification. Additionally, you may study ISACA’s review manual and practice its question bank.
Ans – It is an association of experts started in 1969 and is globally accredited, originally known as the Information Systems Audit and Control Association. ISACA-certified professionals always hold an edge over others in professional courses.
Ans – The UAE has been showing an aggressive push towards digital transformation over the past few years. Thus, cybersecurity resilience and regulatory compliance are a need of the hour in almost every digitised industry.
